Identity and Access Management (IAM)⚓︎
Allow vs Deny⚓︎
In IAM, the interplay between "allow" and "deny" statements determines resource access. If any "deny" statement is present in the policy, access is denied, regardless of any "allow" statements. The default behavior is to deny resources, and explicit "allow" statements are required for access.
LDAP⚓︎
LDAP, or Lightweight Directory Access Protocol, is a software protocol enabling the location of data about organizations, individuals, and other resources in a network.
Identity Federation⚓︎
Identity federation establishes a trust system between two parties to authenticate users and convey necessary information for authorizing their access to resources.
User Groups⚓︎
User groups in IAM are designed exclusively to contain users.
S3 Bucket Policies vs Access Permissions⚓︎
- S3 Bucket Policies:
- Used to add or deny permissions across some or all S3 objects in a bucket, facilitating central management.
- Grants access to users within an AWS account or other AWS accounts.
- Offers restrictions based on request time, SSL usage, and requester IP address using policy keys.
- User Access to S3:
- Governed by IAM permissions.
- Instance (EC2) Access:
- Governed by IAM roles.
- Public Access to S3:
- Controlled by bucket policy.
| Type of Access Control | Account Level Control | User Level Control |
|---|---|---|
| IAM Policies | No | Yes |
| ACLs | Yes | No |
| Bucket Policies | Yes | Yes |
IAM Credentials Report⚓︎
IAM Credentials Report is a security tool that provides a comprehensive list of AWS accounts, IAM users, and the status of their various credentials. It is valuable for auditing permissions at the account level.
IAM Access Advisor⚓︎
IAM Access Advisor offers insights into the service permissions granted to a user and when those services were last used. This information aids in revising policies at the user level.
AWS Policy Simulator⚓︎
The AWS Policy Simulator is a tool used to test and troubleshoot IAM policies attached to users, user groups, or resources.
Identity and Access Management Access Analyzer⚓︎
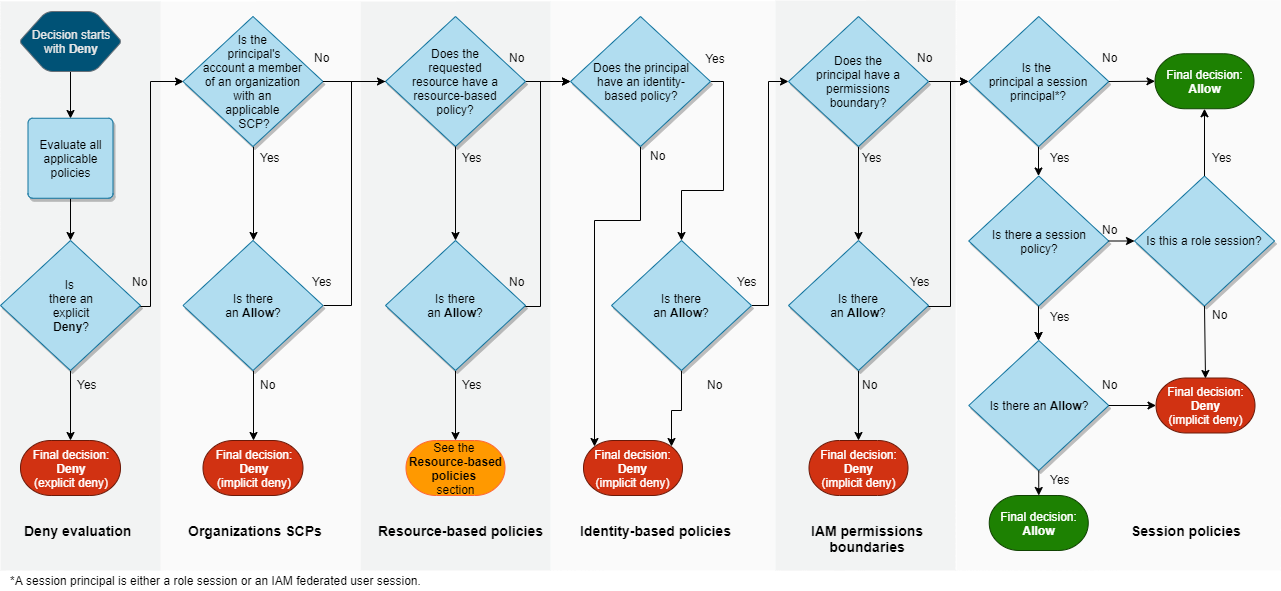 Identity and Access Management Policy Evaluation Logic
Identity and Access Management Policy Evaluation Logic
Amazon Cognito⚓︎
Amazon Cognito serves as a web identity federation service and identity broker. Key features include:
- Handles interactions between applications/resources and Web Identity Providers (IdPs).
- Synchronizes data across multiple devices using SNS for notifying devices associated with a user upon data deltas.
- User Pool: Manages user registration, authentication, and account recovery. Compatible with IdPs like Facebook, Amazon, Google, Apple, OpenID Connect providers, and SAML.
- Identity Pool: Receives authentication token to authorize access directly or through the API Gateway. Maps to IAM roles for authenticated/guest users.
AWS Resource Access Manager (RAM)⚓︎
AWS Resource Access Manager facilitates resource sharing across AWS accounts. Key points include:
- Sharing Resources: Allows sharing of resources owned by one AWS account with other accounts (within an Organizational Unit or any account).
- Preventing Duplication: Aids in avoiding resource duplication by sharing VPC subnets, AWS Transit Gateway, Route 53 Resolver Rules, and License Manager Configurations across accounts.
- Limitations: Certain restrictions apply, such as sharing VPC subnets within the same OU and limitations on managing others' resources.